
A logo is pictured outside a Jaguar Land Rover new car show room in Tonbridge, south east England, on May 24, 2020. Jaguar Land Rover (JLR), owned by India's Tata Motors, was on Sunday said to be in talks with Britain's government in the hope of to securing a loan following a drop in sales due to the COVID-19 coronavirus pandemic. (Photo by Ben STANSALL / AFP)
Published: 6 September 2025 (BST)
Summary: Jaguar Land Rover (JLR) shut down systems this week after a major cyber incident that has severely disrupted production and retail operations. Factories have told staff to stay home until at least Tuesday 9 September, while JLR continues a controlled recovery. The company says there’s no evidence customer data has been stolen. Unverified claims of responsibility have appeared on Telegram (including a persona “Rey,” linked by some analysts to Hellcat/Scattered Spider/ShinyHunters), but JLR has not confirmed attribution. ReutersThe GuardianJaguar Land RoverFinancial Times
Alt: Minimalist padlock and car graphic with title text “JLR Cyber Incident — UK manufacturing outage — Sept 2025”. (Original artwork — CC0/public domain)
What’s confirmed (and what isn’t)
- Confirmed by JLR (2 Sept): “Immediate action” taken, proactive shutdown, no evidence of customer data theft; restoring global applications in a controlled manner. Jaguar Land Rover
- Operational impact (5 Sept): Production and retail severely disrupted; factory staff told to stay home until at least Tue 9 Sept while recovery proceeds. ReutersThe Guardian
- Attribution: Media and researchers cite unverified claims on Telegram (e.g., “Rey”) and links to Scattered Spider/Lapsus$/ShinyHunters/Hellcat ecosystems. JLR hasn’t attributed the attack. Treat these claims as unconfirmed. The GuardianFinancial Times
Incident timeline (BST)
Alt: Timeline showing detection, public statement, claims of responsibility, staff stay-home advisory, and earliest return date.
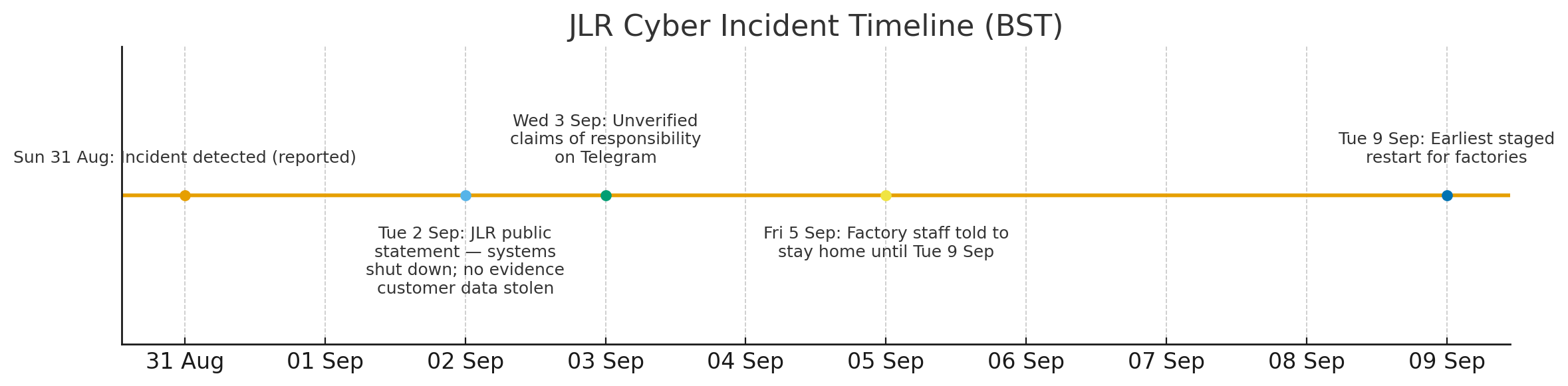
- Sun 31 Aug: Incident reportedly detected; systems begin going offline as precaution. The Guardian
- Tue 2 Sept: JLR public statement: systems shut down to mitigate impact; no evidence of customer data theft; restoration to proceed in a controlled manner. Jaguar Land Rover
- Wed 3 Sept: Unverified claims of responsibility appear on Telegram; media link to Scattered Spider/ShinyHunters/Hellcat ecosystems. The GuardianFinancial Times
- Fri 5 Sept: Staff at multiple UK plants instructed to stay home until Tue 9 Sept while recovery continues. ReutersThe Guardian
- Tue 9 Sept (earliest): Target for initial staged restarts at some sites (subject to change). The Guardian
Technical take: a plausible attack path (based on 2025 UK campaigns)
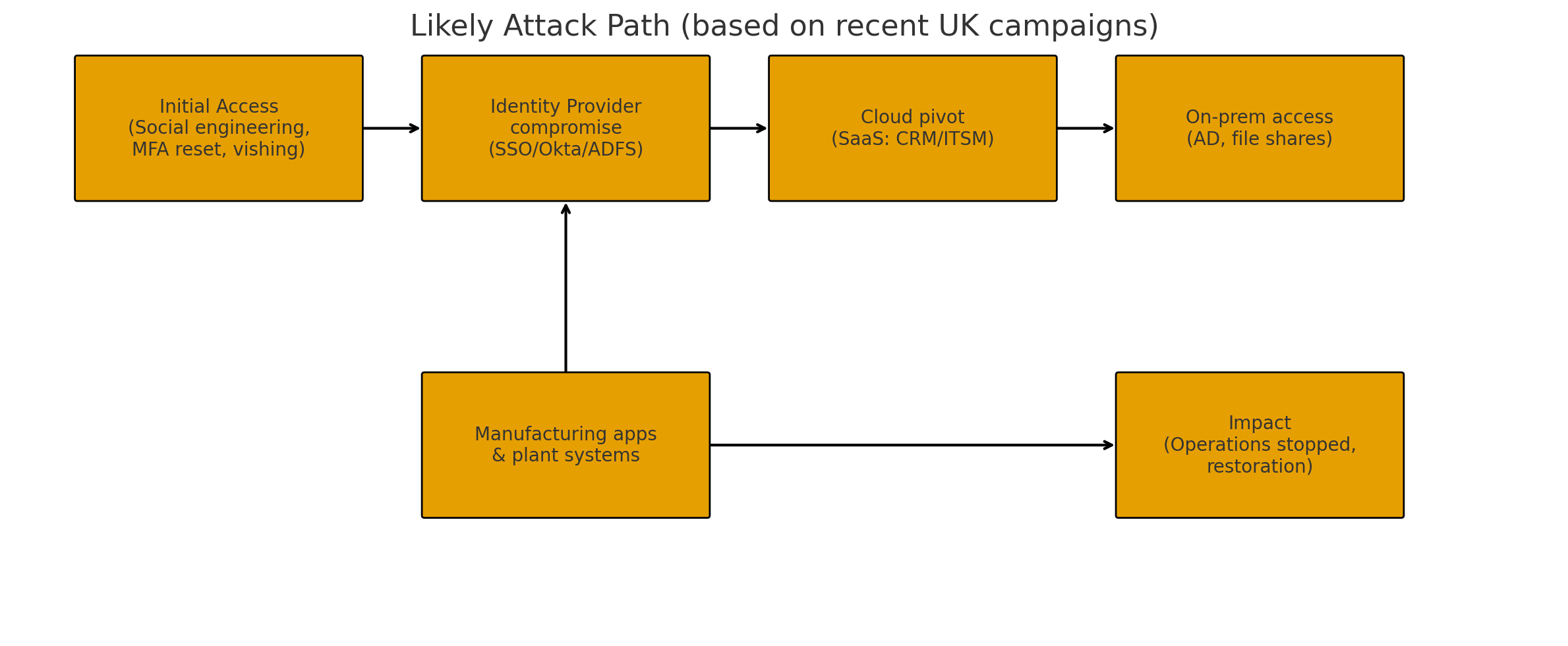
While specifics at JLR aren’t public, recent UK/US campaigns by Scattered Spider and ShinyHunters frequently rely on social engineering (vishing, helpdesk-assisted MFA resets), MFA bypass, and IdP takeover to pivot into SaaS and on-prem. From there, access to build/deployment tooling and shop-floor apps can force operational shutdowns even when no data extortion is visible. Push SecurityReliaQuest+1
Alt: Diagram of likely steps—Social engineering → IdP compromise → Cloud/SaaS pivot → On-prem access → Manufacturing apps → Operational impact. (Original artwork — CC0/public domain)
Recent TTPs to watch:
- Helpdesk social engineering to reset MFA; SIM-swap/vishing for takeover. ReliaQuest
- SaaS pivoting (e.g., Salesforce/ITSM) using session/token theft and OAuth abuse. ReliaQuestThe Hacker News
- Rapid lateral movement & privilege escalation toward identity stores and deployment pipelines. extrahop.com
OT/Manufacturing reality check
Proactive IT shutdowns reduce data loss but can stall production when OT relies on corporate identity, licensing, file shares, or scheduling services. NCSC and allied guidance emphasise segmentation, least privilege, and operational independence for critical plant systems. NCSCU.S. Department of DefenseCanadian Centre for Cyber Security
Recommended Actions for UK Organisations in the First 72 Hours
- Hunt for identity abuse
- Review helpdesk logs for MFA reset calls; correlate with unusual sign-ins and device changes.
- Pull IdP telemetry (e.g., Okta/Azure AD): impossible travel, inactive → admin promotion, MFA method changes, high-risk tokens. Push Security
- SaaS exposure check
- Inspect Salesforce/CRM audit logs: new connected apps, token grants, IP allowlist edits, data export spikes. ReliaQuestThe Hacker News
- Containment without collapse
- If compromise suspected, stage controls: isolate admin accounts, rotate secrets, invalidate sessions; avoid “hard power-offs” on critical OT unless safety demands it. Follow NCSC incident management steps. NCSC
- Legal & regulatory posture
- Verify ICO and sector-regulator notification thresholds, and record decision-making. Monitor the Home Office proposals on ransomware reporting/payment restrictions (updated this week). GOV.UK
Hardening plan (30/60/90 days)
30 days
- Helpdesk hardening: caller verification scripts, call-back to HR numbers on file, require FIDO2 re-enrolments in person.
- MFA everywhere with number-matching or passkeys; block SMS.
- Admin separation: break-glass accounts with PAWs; enforce device posture for all admin roles.
- SaaS security baselines: least-privilege OAuth scopes; alert on new connected apps; disable legacy auth. Push SecurityNCSC
60 days
- IdP change control: approvals & logging for MFA resets, app assignments, group changes.
- Network segmentation for OT: logical/physical isolation, one-way data diodes where practical; distinct identity/backup for plant. NCSCU.S. Department of Defense
- Immutable backups & restore drills: time-boxed tabletop + technical restore exercises tied to stated RTO/RPO.
- SaaS egress governance: DLP guardrails on large exports; IP ranges/Private Connect where available.
90 days
- Threat-led testing (TLPT): simulate vishing + helpdesk + IdP takeover chain.
- Board readiness: NCSC board toolkit adoption; incident comms playbooks prepared and rehearsed. NCSC
- Supplier posture: require IdP posture/MFA & incident reporting in contracts; validate with evidence.
Detection engineering quick wins (examples)
- Helpdesk-assisted MFA reset spike
Signal: ≥3 MFA resets for staff in one department in 24h + new device enrolments. - IdP risky admin change
Signal: Admin role grant followed by OAuth app create within 30 minutes from new ASN. - SaaS bulk export anomaly
Signal: Salesforce “Data Export” or unusually large Report Exports outside business hours.
(Implement as SIEM rules or Sigma; tune to your IdP/SaaS stack.)
Lessons learned (so far)
- Identity is the blast door. Modern crews frequently skip malware and go straight for helpdesk + MFA reset → IdP → SaaS/AD. Assume this path and instrument accordingly. ReliaQuest
- Operational interdependence hurts. If plant requires corporate IT (IdP, file shares, license servers), IT recovery = OT recovery. Design for degraded offline modes. NCSC
- Attribution takes time. Treat Telegram bravado as background noise until verified by forensics/law enforcement. The Guardian
- Governance matters. With UK proposals tightening ransomware reporting/payments, boards need rehearsed decision paths and records. GOV.UK
Useful references & further reading
- JLR official statement (2 Sept): proactive shutdown; no evidence of customer data theft. Jaguar Land Rover
- Reuters: continuing disruption; staff to stay home; controlled restoration. Reuters
- The Guardian: discovery on Sunday; attribution claims remain unverified. The Guardian
- TTP background: Scattered Spider/ShinyHunters 2025 playbooks and SaaS campaigns. Push SecurityReliaQuest+1
- NCSC (UK): incident management; OT security collection; board toolkit. NCSC+2NCSC+2




